Cybersecurity
Cybersecurity is comprised of practices, processes, and technologies to assist in protecting systems, networks, and data from malicious intent and unauthorised access (De Groot 2020).
The current state of cybersecurity in Australia reportedly paints a damning picture. During the 2020-21 financial year, the Australian Cyber Security Centre (ACSC) reported that there were over 67,500 cybercrime incidents which have increased by 13% from the previous year (Australian Signals Directorate (ASD) et al. 2021). Furthermore, government organisations are not immune to cyber-attacks, as, in July of 2021, the New South Wales’s Department of Education fell victim to a malevolent cybersecurity incident. Systems were disrupted and taken offline just as students and teachers took their learning online due to the Covid-19 lockdown (Tan 2021). As technological advancements continue to make headway, so do the cyber security incidences. According to Veerasamy (2020), cybercrime usually takes place for monetary gain, while malicious individuals and groups carry out hacking and other cyber-exploitation for excitement and ‘clout’, which by modern definitions is to boost one’s ego.
Figure 1: An enactment of a cyberattack unfolding and its
consequences. (Cisco, n.d.)
(This video shows the devastating effects a
cyberattack on a company can occur and how easy it is for a hacker to
gain and hold ransom data that is illegally obtained)

Figure 2:Global
Cybercrime Damage by 2021 (Chang 2021)
(This infographic depicts a grim
future that cybercrime has penetrated everyday life and continues to
cause significant economic losses)
In the public sector, the Australian Government is actively providing resources for increasing cyber security awareness (DIIS, 2018). Additionally, concerning businesses and larger corporations, routine employee training aimed at cybersecurity topics and regular revision of Information Technology (IT) procedures and policy needs to take place (Tellier 2018). Cybersecurity for government organisations can be improved through extensive multi-layer use of user-friendly authentication solutions, biometric security measures like fingerprint sensors and face-recognition software, and notably, by having a prudent plan that addresses authentication (Chertoff & Grant 2017).
Through incidents such as the Sony and, more recently, Facebook hack, it has been proven that passwords alone are not adequate. Multi-factor authentication (MFA) will be commonplace in cloud services and web applications (Walker 2020). In larger organisations, mass digital transformation has begun to take place as Covid-19 acted as the catalyst in driving the need for remote work. Companies and Governments will review and improve their IT processes and procedures through better education and adopting newer security technologies (Brooks 2021).
Several notable technologies make cybersecurity implementation possible. Firstly, through Blockchain, a technology mainly used for cryptocurrency, government agencies such as the National Health Service (NHS) of England have begun to use this technology to encrypt and secure data (Sturman 2020). Secondly, Artificial Intelligence (AI) technology is more adept at detecting cyber-attacks and data breaches using refined algorithms. Through machine learning, systems are trained to spot malware and ransomware and run pattern recognition before they occur (Belani 2021). Thirdly, Multi-factor authentication (MFA) uses a combination of elements to authenticate (Walker 2020).
-
Knowledge
Personal information, including maiden names, phone numbers and pet names. -
Possession
One-time password (OTP) generating tokens or applications. -
Inherence
Metrics intrinsically owned by the authorised user in the form of fingerprints and voice recognition. -
Location-based
Using the user's IP address to determine location. -
Risk-based
By analysing the user’s behaviour, for example, the time the access is requested, whether the user is using a private or public network and the consistency in devices being used.
As these cybersecurity technologies continue to develop rapidly, the threats and cyber-attacks will become more sophisticated. There are escalating concerns that these technologies will worsen the inequality between the technology-versed and the technology-illiterate. However, with the implementation of technologies such as Blockchain, AI and MFA, alongside adequate education and cyber-awareness, building a cyber-resilient society is possible (Kavanagh 2019).
It is possible that the increase in cybersecurity breaches is greater than ordinary citizens can fathom. In Australia, a new government bill was introduced in August 2021 to give the police more power to spy on cybercriminal suspects online. Kieran Pender, a senior lawyer at the Human Rights Law Centre, stated that the bill’s powers ‘are unprecedented and extraordinarily intrusive; they should be narrowed to strictly necessary and subject to robust safeguards’ (Karp 2021).
In 2004, The Council of Europe Convention on Cybercrime (Budapest Convention) was in effect to focus on unifying laws and expanding alliances across countries so that all sorts of cybercriminal activity such as denial of service (DDoS) attacks, malware, or online scams could be prosecuted in the affected countries (Daskal & Kennedy-Mayo 2020). While this treaty is considered to be exhaustive in dealing with cybercrime, it has been condemned for not protecting human rights adequately (Brown 2021). Therefore, as cybercrimes and cybersecurity breaches continue to increase at an alarming rate, there could be less privacy and rights for everyone.
In countries like China and Russia, governments have effectively been granted ‘cyber sovereignty due to their rampant cybercrime occurrences. Practices considered objectionable to other democracies, like extreme online censorship and control of internet gateways, are used to monitor their citizens. Other technologies such as facial recognition technologies and data mining are also used to spy on potential cybercriminals (Sherman 2019).
Mass digital transformation for for-profit organisations and not-for-profit organisations will take place. With many now working from home or attending school and universities online, it is inevitable that the threat of cybersecurity breaches will escalate. This will lead to the Government stepping in to protect their citizens, potentially granting them too much power in monitoring and eroding human rights (Mulaomerovic 2021).
According to the US Bureau of Labor Statistics, careers in cybersecurity are tipped to grow by 31 per cent by 2029 (Paykamian 2021). Burning Glass Technologies (2020) reported that as global cybersecurity face new challenges at an exponential rate, new skills will be required in combatting them. In areas such as application development security and cloud security, the high demand will come with significant salary premiums. Occupations such as software developers, systems engineers and network architects will be required to possess these skills. To follow suit, the demand for cybersecurity or IT-related education will increase. Institutions and organisations will devote more resources to cybersecurity programs and training (Paykamian 2021).
Regarding technologies, single password authentication will be made redundant as MFA technologies are developed further. With cloud storage technology deemed more secure than local storage, consumer hardware for data storage will also see a decrease (Weaver 2021). Additionally, new technologies will need to be put in place. For example, at International Business Machines Corporation (IBM), cybersecurity-related services such as Security as a Service (SaaS) and Secure Access Service Edge (SASE) are available for businesses. Newer technologies are constantly being developed as part of their offerings (Jha 2021).
Cybersecurity anxiety is on the rise in the modern world. According to Dr Maria Bada (2020), “The psychological effects of cyber-attacks may even rival those of traditional terrorism.” It is unavoidable that the increase in cybersecurity breaches is taking a psychological toll on the general population (Guynn 2020).
Personally, there is a change in purchasing habits to favour technology products such as phones with better Security and e-commerce websites with better authentication. Additionally, access to personal data, including online banking services, government websites and even social media, may be restricted due to MFA technologies. However, on a positive note, cybersecurity-related professions are in demand, and as a student in IT, this is good news.
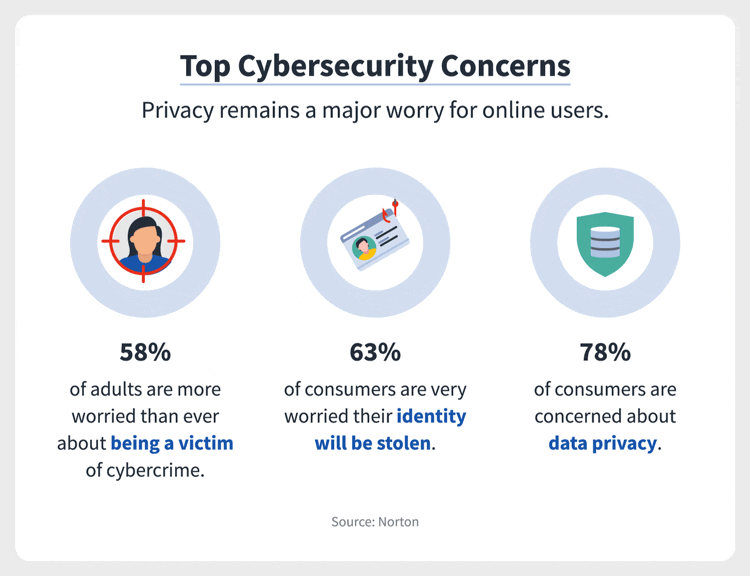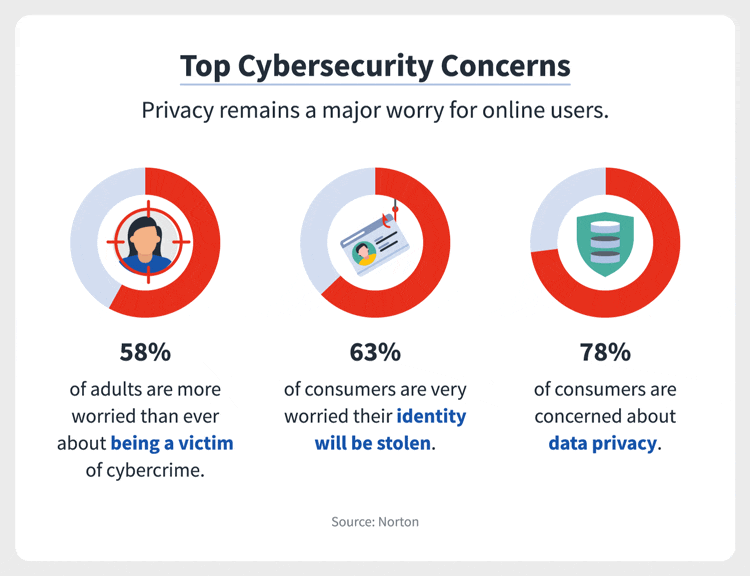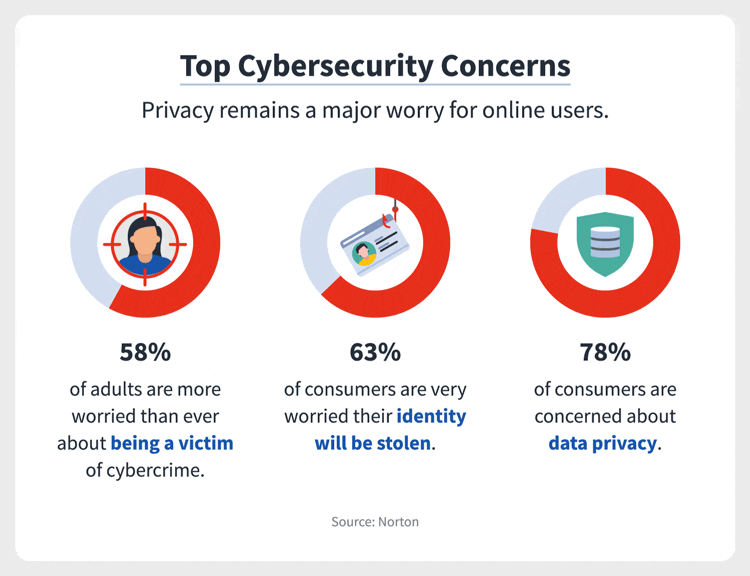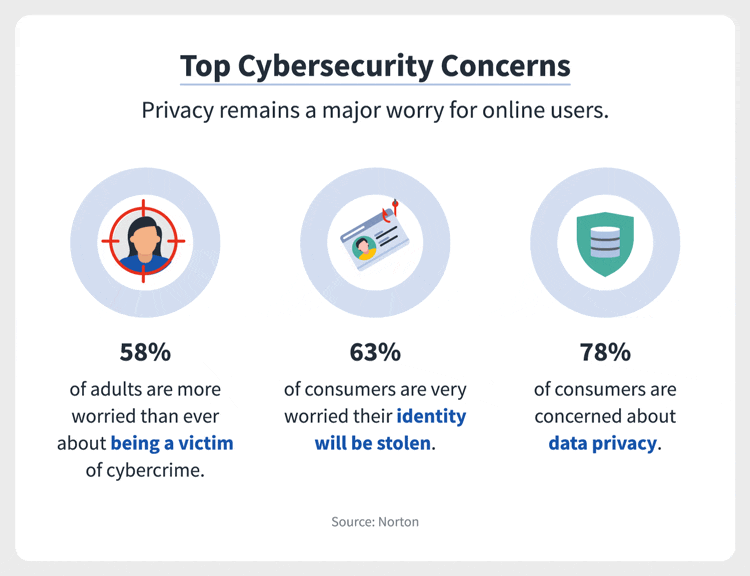
Figure 3: Top Cybersecurity Concerns (Stouffer 2021)
(This infographic
highlights the top cybersecurity concerns by the general public. Observed
is a 78 percentage of consumers who are concerned about data privacy,
followed by 63 per cent who are very worried that their identity will be
stolen and 58 per cent who are worried about being a victim of cybercrime.
This data informs us that an above-average number of people are concerned
about the state of cybersecurity)
As the gap of cybersecurity knowledge grows, the uneducated will become easy targets for cybercriminals. This will require the governments to step in to try and protect their citizens by educating and sending warnings. Data breaches will also become common with the increased consumption of social media by children (Rachwani 2021). As a parent of a young child, measures are taken at home to secure data privacy during the usage of devices such as iPads and mobile phones, albeit being restrictive in nature. As a daughter to elderly parents, a wider gap of knowledge is observed as the older generation are less aware of the state of cybersecurity and are more likely to be affected. In turn, the level of anxiety increases as cyber criminals become more innovative in their illegal activities.
In conclusion, developing cybersecurity technology is a response to a cybercrime pandemic. Much like the Covid-19 virus and its vaccine, if this technology is undermined, the losses may not be known right away but will be destructive when it surfaces. Our addiction to data consumption will likely continue at an exponential rate, and it is imperative that cybersecurity be considered at every level.
References
- Australian Signals Directorate (ASD), Australian Defence Intelligence Organisation (DIO), Australian Criminal Intelligence Commission (ACIC), Australian Federal Police (AFP), Australian Security Intelligence Organisation (ASIO) & Department of Home Affairs 2021, ACSC Annual Cyber Threat Report 1 July 2020 - 30 June 2021, Australian Cyber Security Centre, 15 September, pp. 12, 15, 17, viewed 27 September 2021, (https://www.cyber.gov.au/acsc/view-all-content/reports-and-statistics/ acsc-annual-cyber-threat-report-2020-21).
- Belani, G 2021, The Use of Artificial Intelligence in Cybersecurity: A ReviewIEEE Computer Society, Computer.org, viewed 27 September 2021, (https://www.computer.org/publications/tech-news/trends/the-use-of-artificial-intelligence-in-cybersecurity).
- Blau, A, Burt, A, Groysberg, B & Yampolskiy, RV 2019, Cybersecurity : the insights you need from Harvard Business Review., Harvard Business Review Press, Boston, Massachusetts.
- Brooks, C 2021, 3 Key Cybersecurity Trends To Know For 2021 (and On ...), Forbes, viewed 27 September 2021, (https://www.forbes.com/sites/chuckbrooks/2021/04/12/3-key-cybersecurity-trends-to-know-for-2021-and-on-/?sh=1f4655214978).
- Brown, D 2021, Cybercrime is Dangerous, But a New UN Treaty Could Be Worse for Rights, Human Rights Watch, viewed 29 September 2021, (https://www.hrw.org/news/2021/08/13/cybercrime-dangerous-new-un-treaty-could-be-worse-rights).
- Burning Glass Technologies 2020, Protecting the Future: The Fastest - Growing Cybersecurity Skills, October, viewed 29 September 2021, (https://www.burning-glass.com/wp-content/uploads/2020/10/Fastest_Growing_Cybersecurity_Skills_Report.pdf).
- Chang, J 2021, 101 Impressive Cybersecurity Statistics: 2020 Data & Market Analysis - Financesonline.com, financesonline.com, viewed 29 September 2021, (https://financesonline.com/cybersecurity-statistics/).
- Chertoff, M & Grant, J 2017, 8 Ways Governments Can Improve Their Cybersecurity, Harvard Business Review, viewed 27 September 2021, (https://hbr.org/2017/04/8-ways-governments-can-improve-their-cybersecurity).
- Daskal, J & Kennedy-Mayo, D 2020, Budapest Convention: What is it and How is it Being Updated?, Cross-Border Data Forum, viewed 29 September 2021, (https://www.crossborderdataforum.org/budapest-convention-what-is-it-and-how-is-it-being-updated/).
- De Groot, J 2020, What is Cyber Security? Definition, Best Practices & More, Digital Guardian.
- Department of Industry, Innovation and Science 2018, What is the Government doing in cyber Security?, Australian Government.
- Guynn, J 2020, Anxiety, depression and PTSD: The hidden epidemic of data breaches and cyber crimes, USA TODAY, viewed 29 September 2021, (https://www.usatoday.com/story/tech/conferences/2020/02/21/data-breach-tips-mental-health-toll-depression-anxiety/4763823002/).
- Jha, P 2021, IBM Finally Rolls Out New SASE Services With Zscaler, Toolbox.com, viewed 29 September 2021, (https://www.toolbox.com/tech/security/news/ibm-finally-rolls-out-new-sase-services-with-zscaler/).
- Karp, P 2021, Australian powers to spy on cybercrime suspects given green light, The Guardian, viewed 29 September 2021, (https://www.theguardian.com/australia-news/2021/aug/25/australian-powers-to-spy-on-cybercrime-suspects-given-green-light).
- Kavanagh, C 2019, New Tech, New Threats, and New Governance Challenges: An Opportunity to Craft Smarter Responses?, Carnegie Endowment for International Peace, viewed 27 September 2021, (https://carnegieendowment.org/2019/08/28/new-tech-new-threats-and-new-governance-challenges-opportunity-to-craft-smarter-responses-pub-79736).
- Mulaomerovic, N 2021, Reexamining Cyber Security in the Context of Human Rights, UNA-NCA Snapshots, viewed 29 September 2021, (https://medium.com/una-nca-snapshots/reexamining-cyber-security-in-the-context-of-human-rights-bd0a1cebba2d).
- Paykamian, B 2021, Cybersecurity Studies Increasingly Popular at US Colleges, GovTech, viewed 29 September 2021, (https://www.govtech.com/education/higher-ed/cybersecurity-studies-increasingly-popular-at-us-colleges).
- Rachwani, M 2021, Facebook data leak: Australians urged to check and secure social media accounts, The Guardian, viewed 29 September 2021, (https://www.theguardian.com/technology/2021/apr/05/facebook-data-leak-2021-breach-check-australia-users).
- Sherman, J 2019, How Much Cyber Sovereignty is Too Much Cyber Sovereignty?, Council on Foreign Relations, viewed 29 September 2021, (https://www.cfr.org/blog/how-much-cyber-sovereignty-too-much-cyber-sovereignty).
- Stouffer, C 2021, 115 cybersecurity statistics and trends you need to know in 2021, Norton.com, viewed 29 September 2021, (https://us.norton.com/internetsecurity-emerging-threats-cyberthreat-trends-cybersecurity-threat-review.html).
- Sturman, C 2020, The first comprehensive blockchain-supported Personal Care Record Platform has been launched | Digital Healthcare, Healthcare Global, viewed 27 September 2021, (https://healthcareglobal.com/digital-healthcare/first-comprehensive-blockchain-supported-personal-care-record-platform-has-been-launched).
- Tan, A 2021, NSW department of education hit by cyber attack, ComputerWeekly.com, viewed 27 September 2021, (https://www.computerweekly.com/news/252503836/NSW-department-of-education-hit-by-cyber-attack).
- Tellier, M 2018, A Practical Strategy to Engage the Workforce Against Cyber Criminals, Security Magazine, viewed 27 September 2021, (https://www.securitymagazine.com/blogs/14-security-blog/post/89100-a-practical-strategy-to-engage-the-workforce-against-cyber-criminals).
- Veerasamy, N 2020, Emerging Cyber Threats and Cognitive Vulnerabilities, Elsevier Science & Technology, London.
- Walker, D 2020, Passwords are not enough: the case for multi-factor authentication, Acuity Mag, viewed 27 September 2021, (https://www.acuitymag.com/technology/passwords-are-not-enough-the-case-for-multi-factor-authentication).
- Weaver, A 2021, What Is the ‘the Cloud’ and Is My Data Safe There?, Hacked.com, viewed 29 September 2021, (https://hacked.com/what-is-the-the-cloud/).
- What Is Cybersecurity? n.d., Cisco, viewed 29 September 2021, (https://www.cisco.com/c/en_au/products/security/what-is-cybersecurity.html?socialshare=lightbox1).